Media
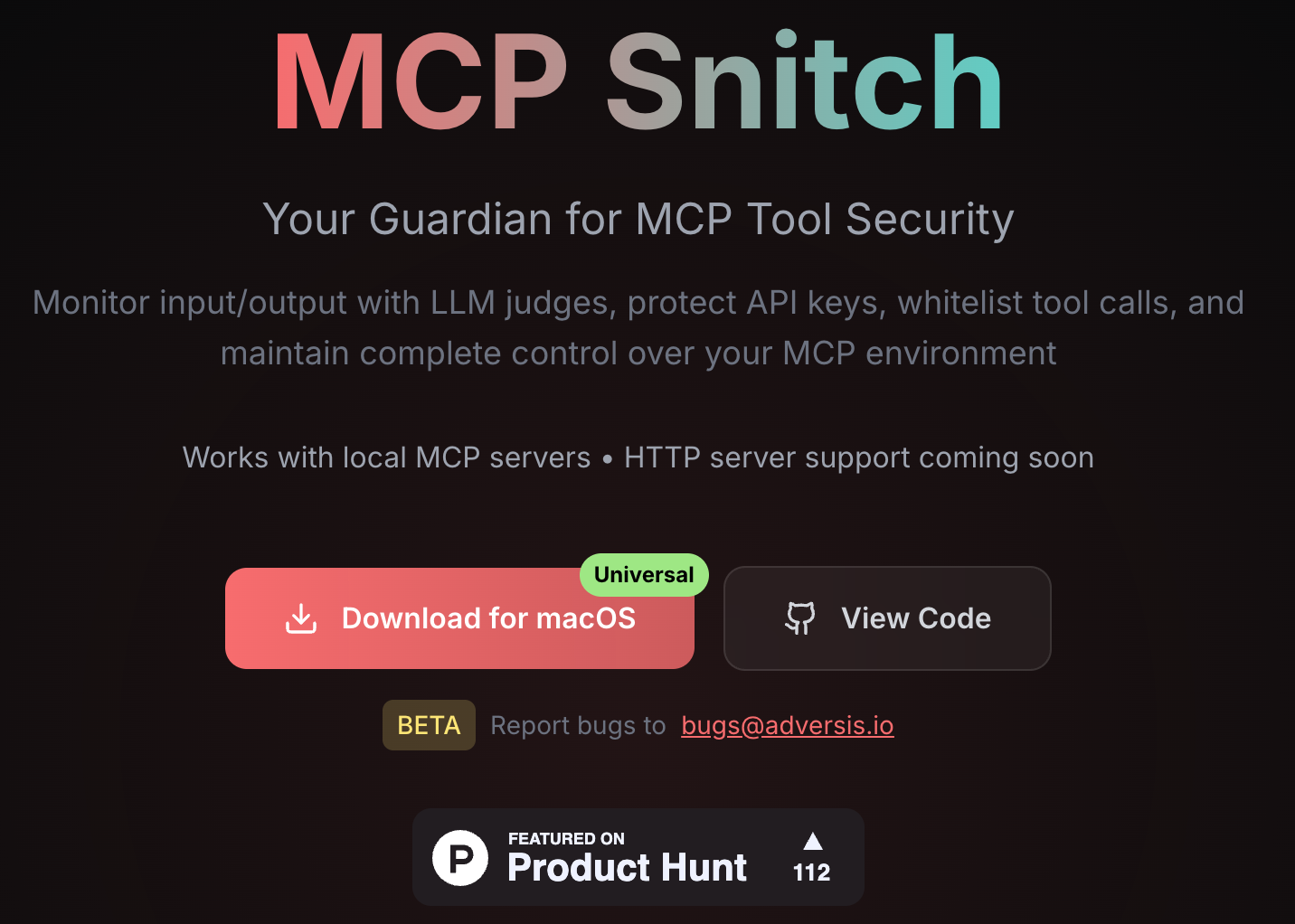
The MCP Security Tool You Probably Need - MCP Snitch
Your Guardian for MCP Tool Security Monitor input/output with LLM judges, protect API keys, whitelist tool calls, and maintain complete control over your MCP environment

Sample Web App Penetration Test Report
Check out a sample penetration testing report with clear and concise findings, and realistic fixes.
Resources
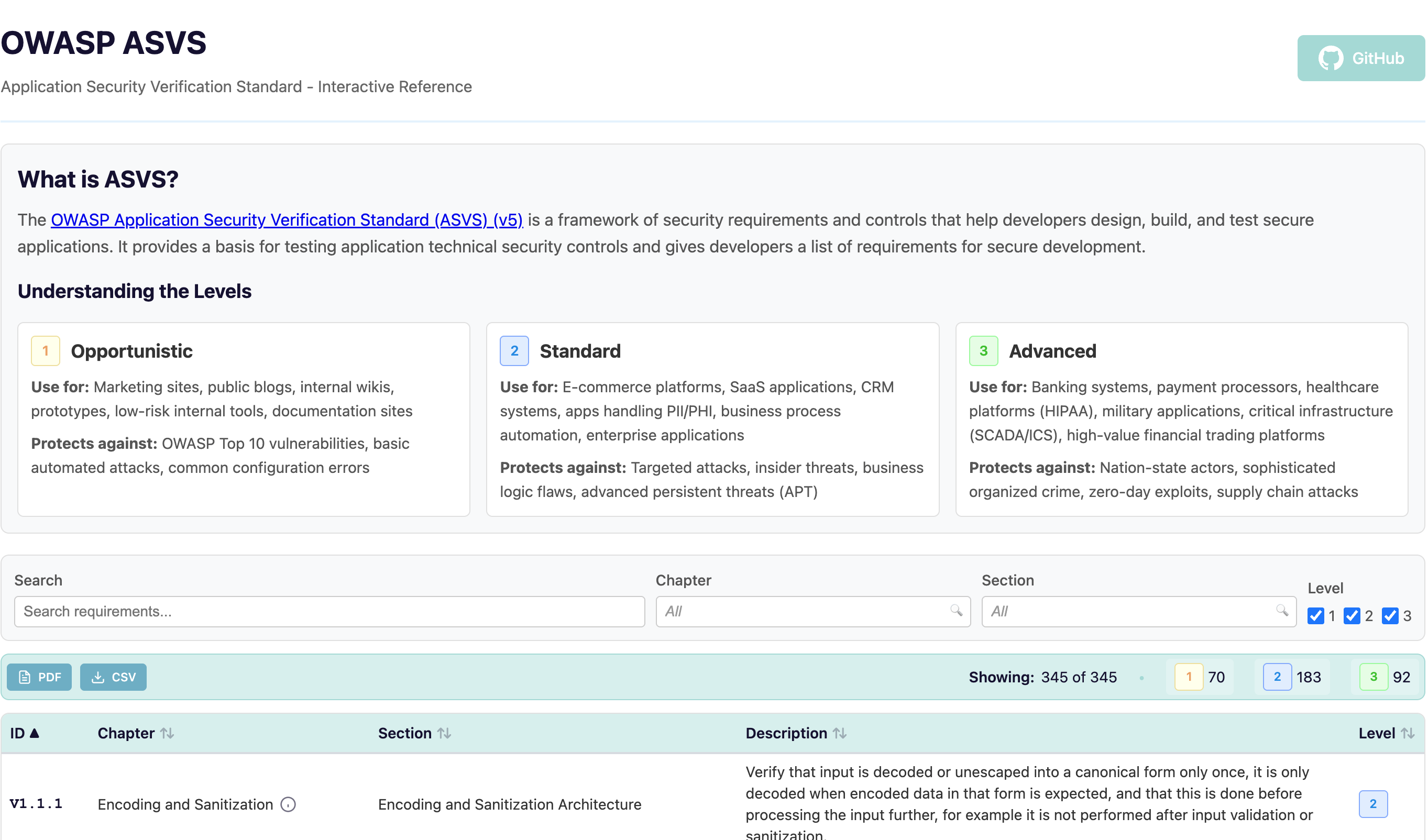
Interactive OWASP ASVS Explorer
We built an interactive wrapper around the OWASP ASVS standards for easy exploration and filtering.
This is some text inside of a div block.
This is some text inside of a div block.

Manufacturing Resilience Expert Joins Adversis
Chad Nelson joins Adversis to lead business development for manufacturing and industrial clients
This is some text inside of a div block.
This is some text inside of a div block.
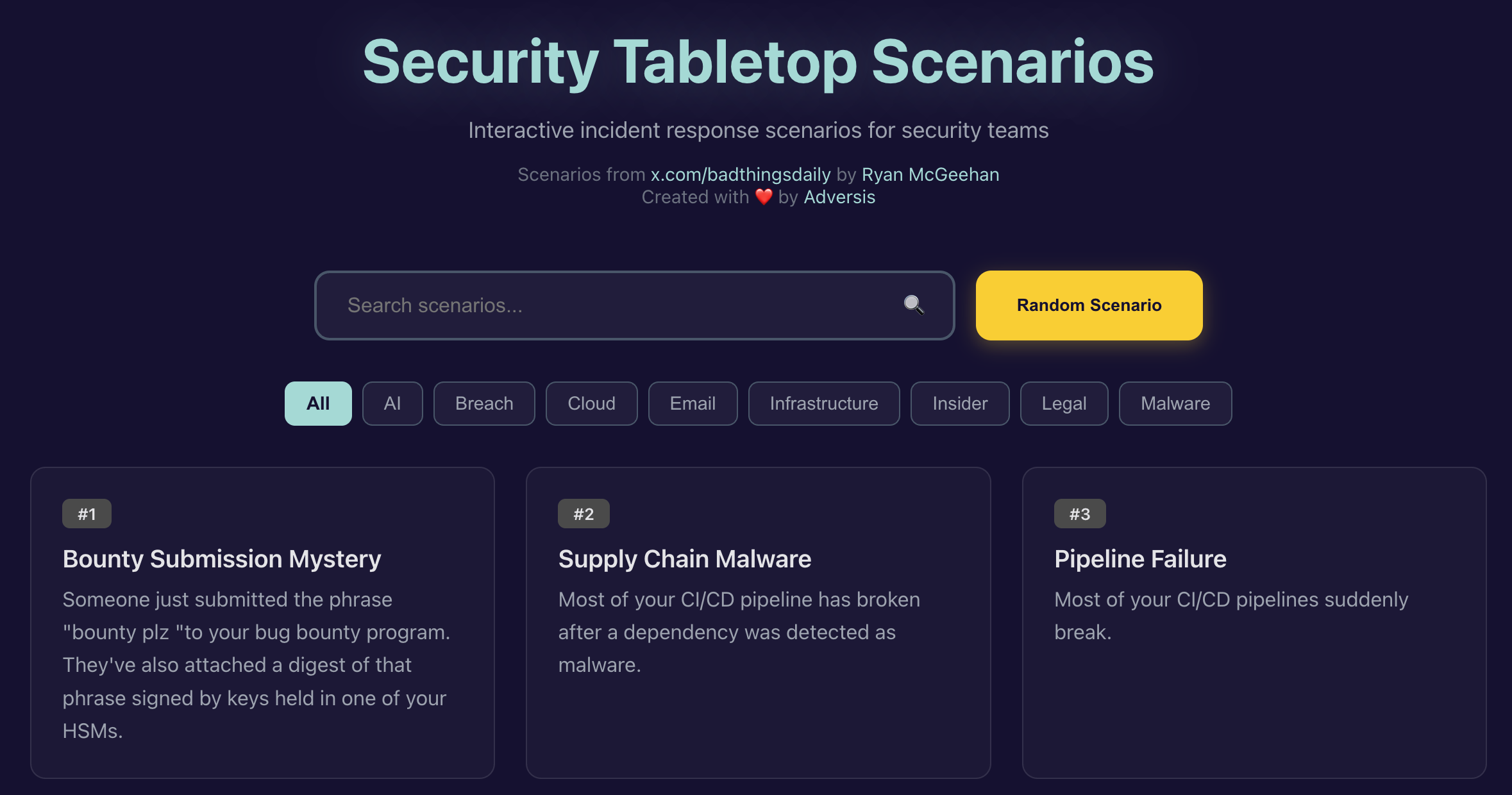
Incident Response Scenarios
Hundreds of interactive incident response scenarios for security teams from the badthingsdaily social media feed
This is some text inside of a div block.
This is some text inside of a div block.
Open Source Tools
Open source penetration testing and assessment tooling to help testers and auditors identify vulnerabilities and protect applications and organizations.
This is some text inside of a div block.
This is some text inside of a div block.

ThreatScan
Get your free attack surface report in 60 seconds - no credit card required.
This is some text inside of a div block.
This is some text inside of a div block.

Cyber Policies
Free cybersecurity policy generator
This is some text inside of a div block.
This is some text inside of a div block.

Startup Security
If you’re a startup founder or stakeholder, read on for a clear actionable guide to implementing effective cybersecurity and compliance measures.
This is some text inside of a div block.
This is some text inside of a div block.

Principles
Secure Architecture is based on repeatability, accessibility, and variability, aka RAV Engineering.
This is some text inside of a div block.
This is some text inside of a div block.

Bad Passwords
Find out what passwords hackers are using to brute force your colleague's accounts (and block those)
This is some text inside of a div block.
This is some text inside of a div block.

SaaS Hardening
Securely configure your SaaS apps to protect your third party accounts and data.
This is some text inside of a div block.
This is some text inside of a div block.

CyberPrices
Get estimated pricing for security assessment services
This is some text inside of a div block.
This is some text inside of a div block.
Articles
A Vishing Crisis Your IT Team Isn't Prepared For

A Practical Defense Guide Against Modern SaaS Attacks
Learn MoreThe MCP Security Tool You Probably Need - MCP Snitch
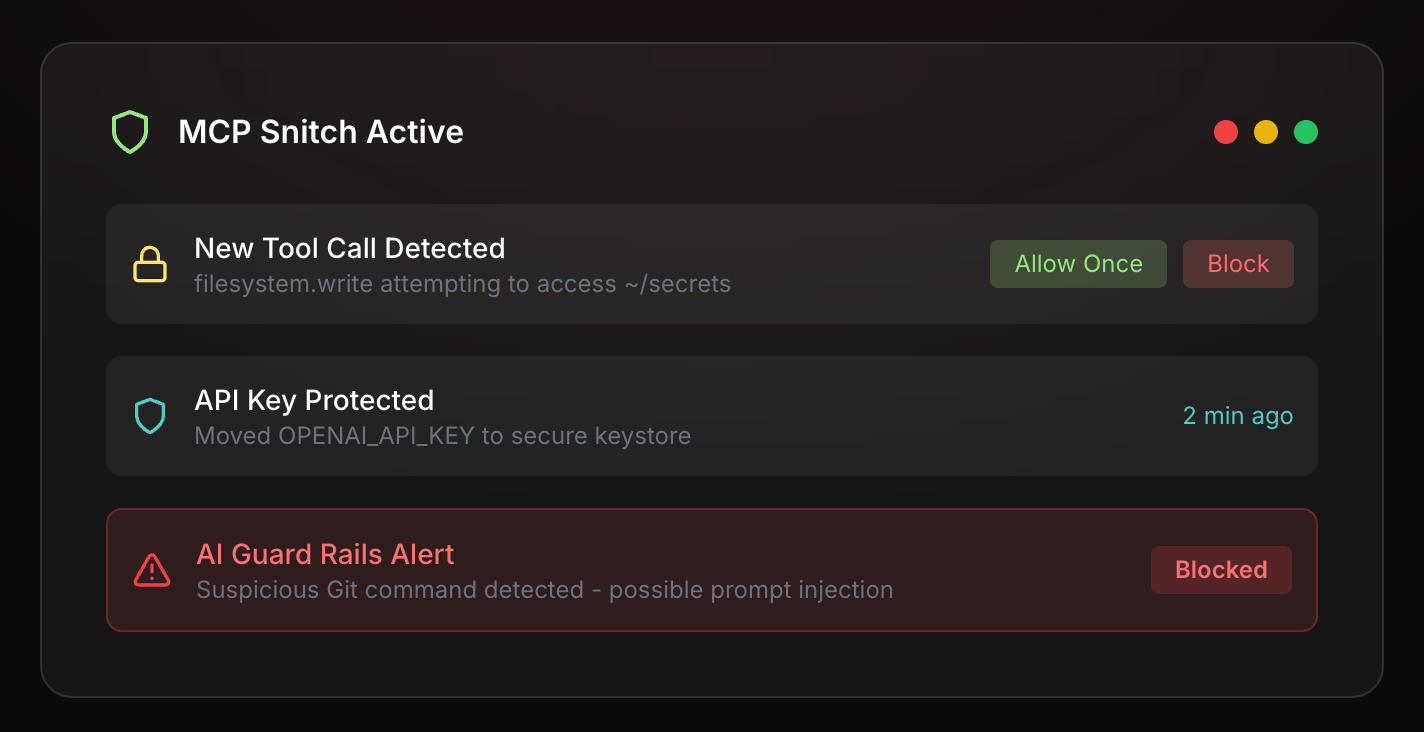
The Model Context Protocol (MCP) has rapidly emerged as the standard for connecting AI agents to external tools and services. However, as the recent GitHub MCP vulnerability demonstrated, the protocol's power comes with significant security challenges. Malicious actors can exploit MCP servers to exfiltrate private data through prompt injection, execute unauthorized operations, or compromise entire systems.
Learn MoreYour MFA Isn't Protecting You: Inside the EvilProxy Campaigns Draining Bank Accounts

How financially-motivated cybercriminals are using EvilProxy to bypass your two-factor authentication, hijack CFO accounts, and why your accounting firm is in the crosshairs
Learn MoreManufacturing Resilience Expert Joins Adversis

Chad Nelson joins Adversis to lead business development for manufacturing and industrial clients
Learn MoreUnpatched Edge Devices are Volt Typhoon's Persistence Point

Strategies to Defend Utilities and Critical Infrastructure Against Volt Typhoon
Learn MoreYour VPN Without MFA is Rhysida's Front Door

Strategies that Work to Defend Aviation and Healthcare Against Rhysida Ransomware
Learn MoreIt's Always a Friday. Phish to Breach.

Another tale from the red team trenches - Okta phish to credit card database breach
Learn MoreYour Newest Employee Might Be a Scammer

How North Korean IT workers are infiltrating American companies through elaborate identity theft schemes
Learn MoreBlind Enumeration of gRPC Services

When you're handed an SDK with no documentation and told "the backend is secure because it's proprietary," grpc-scan helps prove otherwise
Learn MorePrivilege Escalation With Jupyter From the Command Line

A recent penetration test led to an interesting way to escalate privileges on a Jupyter instance running as root.
Learn MoreThe Psychology of Payment Fraud

Fraudsters impersonate vendors and colleagues on the phone and email, abusing our trusting natures and lack of established norms and processes.
Learn MoreWhat Every CFO Needs to Know About Cyber Risk in 2025

Let's talk dollars and cents about what the 2025 Verizon Data Breach Investigations Report means for your bottom line and what you can do about it.
Learn MoreShow Me the Incentives, and I'll Show You the Outcomes

Don't blame people as the weakest link in cybersecurity- blame their incentives.
Learn MoreHow to Write a Hashcat Module

Cracking 389 Directory Server password hashes automatically with the password cracker Hashchat
Learn MoreLiving off Node.js Addons

Swap out compiled Node.js addons with your own code and force a legitimate Electron application load your code
Learn MoreThe Compliance Trap

Does that SOC 2 report actually mean anything? Go beyond compliance with systems thinking.
Learn MoreA Short Red Team Story: Stealing the Crown Jewels

Inside a major data compromise and a few security architecture things you can do today to reduce the likelihood this happens to your organization.
Learn MoreHIPAA Security Rule Updates: A Reality Check and Different Approach

New Proposed HIPAA Security Rule Changes are a $3,000 Fairy Tale. Read on for a Better Approach for Healthcare Organizations
Learn MoreAdversis Partners with Montana Organizations to Support High-Tech Manufacturing

Adversis exhibited with the Montana Department of Commerce and Montana Quantum and Photonics Alliance at SPIE Photonics West 2025, helping firms build resilient operations while meeting compliance requirements.
Learn MoreThink Twice Before You Paste

A Practical Guide to Using AI Tools like ChatGPT Without Compromising Security
Learn MoreSecurity Advisory: Chamber of Commerce Software API Vulnerabilities

Major Chamber of Commerce software platforms have API security gaps exposing member data. The issue affects approximately 4,500 chambers and potentially 1.35 million businesses.
Learn MoreWhy Security Policies Fail

And How to Make Them Work in the Real World: A Pragmatic Approach for Growing Companies
Learn MoreHow to Sell to Enterprises: Avoiding the CISO Veto

The shift is clear: compliance artifacts alone no longer suffice. What matters is demonstrating precise, customer-specific risk reduction. (e.g. competence)
Learn MoreAwareness Alone Is Dumb: How to Make Cybersecurity Habits Stick

How to Make Cybersecurity Habits Stick When Awareness Isn’t Enough. Mantras don't count. You need technology to take the burden and verification to find needles in configuration haystacks.
Learn MoreWhy Your Mid-Market Business Needs a Cybersecurity Advisor

Mid-market business leaders should consider a cybersecurity advisor (vCISO) for a few reasons, all of which Adversis has proven out many times over.
Learn MoreReducing Loan Risks with Cybersecurity Assessments

Banks are beginning to incorporate cybersecurity assessments into SMB loan evaluations, recognizing that weak security practices increase financial risks such as breach costs and operational disruptions. This approach helps reduce default rates, fosters resilience in SMBs, and aligns lending practices with modern business risks.
Learn MoreIt's Getting Harder to Recognize Scams

Generative AI lowers the barrier for scammers to create believable texts, emails, voices, images, and even video. Just like any new technology, this will be an arms race of offense and defense.
Learn MoreStop Letting Contractors Be Your Biggest Security Risk

A streamlined, risk-focused approach to contractor access can secure your network without bogging down productivity.
Learn MoreThe 3 Cybersecurity Awareness Tips Most Likely to Make a Difference

There's so much noise. What should a normal person actually be concerned about?
Learn MoreHow Much Cybersecurity Insurance Do I Actually Need?

Insurance can’t fix what you haven’t secured. Are you overpaying or under-protected?
Learn MoreHow to Achieve GDPR Compliance the Hard Way

Like death and taxes — you can't opt out of GDPR because you don't like it.
Learn MoreRental Car Vendor's Security Flaw Exposed Damage Claims Reports

Legitimate emails with bad practices and an insecure website add insult to injury.
Learn MoreHow to Ask Your Vendors to Verify Their Security Practices

Your vendors' security practices directly impact your own. Ensuring that your partners have robust data security controls in place is not just about peace of mind—it's a regulatory requirement for many industries, especially when dealing with sensitive information.
Learn MoreA Physical Site Security Audit Checklist You Can Actually Use

This audit checklist is designed to guide you through a thorough review of your site’s security based on leading standards from organizations like ASIS International, ISO, NFPA, and BOMA. Let’s break it down into actionable steps, making sure you can spot weak spots and implement fixes without drowning in paperwork.
Learn MorePragmatic Steps to Get CMMC Level 1 Compliant

Get started securing your business as a federal subcontractor with meme driven guidance.
Learn MoreDon’t Let This Simple Mistake Drain Your Bank Account

Are You Making It Easy for Cybercriminals to Steal Your Cash App Balance and Account Access?
Learn MoreNew Healthcare Cybersecurity Performance Goals: Essential vs. Enhanced

The U.S. Department of Health and Human Services (HHS) recently released a concept paper that details the ongoing efforts to enhance cybersecurity in the healthcare and public health sectors.
Learn MoreStrengthening Cybersecurity in the Biotech Industry: Insights from the NSCEB and the Latest Findings

This article explores the cybersecurity challenges in the biotech industry, emphasizing the need for robust frameworks and public-private partnerships. Drawing from recent reports, it highlights strategies to protect sensitive data and biotechnological processes from emerging cyber threats.
Learn MoreUnderstanding FERPA Compliance for Educational Web Applications

FERPA is a vital law that protects the privacy of student educational records. For organizations managing student data through web applications, compliance with FERPA is essential. This involves implementing strong encryption, secure access controls, and clear breach response protocols.
Learn MoreNavigating COPPA Compliance for Web Applications Targeting Children

Ensuring COPPA compliance is not just about meeting legal standards—it's about protecting the privacy and security of children online. By adhering to current requirements and preparing for upcoming changes, organizations can demonstrate their commitment to safeguarding children’s online experiences while maintaining trust with parents and educators.
Learn MoreAn In Depth (and Actionable) Guide to Cybersecurity Table Tops

Incident response tabletop exercises are crucial for preparing your organization to handle cyber incidents. These simulations test your incident response and Business Continuity Plans (BCPs), helping to identify gaps and improve team coordination.
Learn MoreThe M&A Process Through a Cybersecurity Lens

When you’re in the middle of a merger, acquisition, joint venture or divestiture, the clock’s ticking. Deals move fast, and it’s easy to let things slip through the cracks—especially cybersecurity, where things work until they come crashing to a halt.
Learn MoreHow to Safeguard Taxpayer Data and Comply with IRS Publication 4557

Take simple, common sense steps to keep your business and client information safe.
Learn MorePolicies, Procedures, and Playbooks

The terms 'Policies,' 'Procedures,' and 'Playbooks' are often used to establish guidelines and standard practices. They're related but serve different purposes. Here's how they work and interact.
Learn MoreYour EDR Is Worse Than My EDR

Not all endpoint detection and response products are built the same - how capable is yours?
Learn MorePractical Steps for TSA Cybersecurity Compliance at Airports

Helping calm the cyber seas for smoother sailing at airports... sorry, wrong analogy!
Learn MoreSoftware Security for Startups

Your startup should care about cybersecurity, but only sort of.
Learn MoreThe (Un)Surprising Wi-Fi Password Mistake Thousands are Making

Adversis estimates that 10% of networks in the region are using a password with a 406 area code and phone number. Is your Wi-Fi password your phone number?
Learn MoreCyberPrices.io: Cybersecurity Cost Transparency

CyberPrices.io - our latest innovation designed to bring transparency to cybersecurity pricing
Learn MoreSimplify Your Life with a Password Manager

A little learning curve puts you ahead of so many and makes life easier
Learn MoreRefund Rip-offs

Don't get ripped off when you sell things and then take money with Venmo and Cash App
Learn MoreInvisible Thieves: How Payment Diversion Scams Work

Follow along from email hack to payment theft
Learn MoreA Fast Track Guide to Losing Money and Data in Business

How Businesses Get Hacked: A mordant 3-step guide on how to lose money and information.
Learn MoreLessons Learned From a Year of SMB Cybersecurity Assessments

Gaps, assumptions, and missing cyber controls continue to plague SMBs
Learn MoreIs Your Wildix Phone System as Secure as it Could Be?

Don't give hackers access to your internal Wildix chats and voicemails
Learn MoreUnraveling the Secrets of Montana's Internet

Montana. Known for its ruggedness. But how secure are we?
Learn MoreForeScout Secure Connector Local Privilege Escalation

A local privilege escalation in a security tool, who would have imagined..
Learn MoreThe Intriguing World of Ransomware Payments: Exploring Crypto, Hacker Hideouts, and the Art of Cashing Out

Dive into the mysterious world of ransomware payments! Learn about how hackers use digital money like Bitcoin, where they hide, and the sneaky ways they turn stolen money into real cash. Learn about real-life examples of how these cybercriminals operate.
Learn MoreIs your MSP secure?

What security measures do you have in place to protect my systems and information?
Learn MoreA BigCommerce Security Primer

BigCommerce is an eCommerce platform that quite a few large brands use. Let's take a look at how to make sure our BigCommerce store is configured securely.
Learn MoreYour Documents, ShareFile'd

Adversis did some brief public research on Citrix ShareFile websites and found over 9,000 customer subdomains, over half of which have links accessible to anyone who can identify them. It’s possible your company is among them.
Learn MoreYour SSN Isn't a Secret

Your Social Security Number is not supposed to be sensitive. It's an ID, nothing more. Unfortunately, more and more platforms and online systems use it to verify your identity.
Learn MoreYour Reconciliation Nightmare - How Attackers Target Payment Flows

Payment Flows. Thanks to platforms like Stripe, they are incredibly simple to implement and manage.
Learn MoreA Safe and Sound Shopify Shop

So you've opened a Shopify store. That's great news! Chances are, you're making something really special and we're excited to help make you and your customers experience secure.
Learn MorePandora's Box: Another New Way to Leak All Your Sensitive Data

Yes, the cloud is still leaking data. This time, we can't blame the SRE team though, everyone has been sharing files publicly, yes, even you probably.
Learn More






